When to Use What Automation Tool
Right, let’s settle this once and for all. I get asked this question every single week: “Richard, should I learn pyATS or just stick with Ansible?” or what is better “pyats vs ansible” or “What about NAPALM – isn’t that simpler?” Look, I’ve been working with all these tools for years, and I’ve seen engineers waste months going down the wrong path because nobody explained when to use what.
Cisco pyATS Blog Index
Don’t be like the bloke from last month’s course who’d spent six months trying to make Ansible validate BGP convergence times. Absolute nightmare that was. Could’ve saved himself loads of aggro if he’d understood what each tool’s actually good for.
So here’s what I’m going to do. I’ll walk you through the main automation tools you’ve probably heard about – pyats vs ansible, NAPALM, and Nornir – and explain exactly when you should use each one. No marketing nonsense, just honest advice based on what actually works in production.
The Fundamental Difference Everyone Gets Wrong
Before we dive into specific tools, you need to understand something that’ll save you months of frustration. There are two completely different types of network automation, and most people mix them up:
Configuration Management: Pushing configs to devices, making sure they’re applied correctly, managing changes. Think of it as “make the network look like this.”
Testing and Validation: Checking that your network’s actually doing what you think it is. This is “prove the network works like this.”
Now here’s where it gets interesting. Most automation tools were designed for the first bit – configuration management. They were built for servers, where you install software, copy files, restart services. Job done.
But networks? Networks are different beasts entirely. Pushing a config is just the start. The real question is whether your OSPF neighbours came up, whether your BGP routes are propagating correctly, whether failover’s working as expected. You can’t just configure something and assume it works.
This is why I see so many engineers struggling. They try to use configuration management tools for testing and validation, then wonder why it’s such a mess.
pyATS vs Ansible: The Configuration Management King

Let’s start with Ansible since everyone seems to know about it. Ansible’s brilliant at what it was designed for – configuration management across lots of devices.
What Ansible Actually Does Well
Agentless simplicity: Nothing to install on your devices. Uses SSH connections you’ve already got. Dead simple to get started.
Massive community: Loads of network modules already written. Chances are someone’s already solved your configuration problem.
Declarative approach: You describe what you want the end state to look like, Ansible figures out how to get there.
Great for compliance: Ensuring all your devices have the same baseline configs, security settings, that sort of thing.
Here’s where Ansible shines – I had a customer with 500 switches that needed identical security configs. Ansible knocked that out in an hour. Would’ve taken weeks doing it manually.
# This sort of thing is where Ansible's magic
---
- name: Configure security baseline on all switches
hosts: switches
tasks:
- name: Set login banner
ios_banner:
banner: login
text: "{{ security_banner }}"
- name: Configure access lists
ios_config:
lines:
- access-list 10 permit 172.16.0.0 0.0.255.255
- access-list 10 deny any
Where Ansible Starts to Struggle
Testing and validation: Ansible can push configs, but can it tell you if OSPF convergence took too long? Can it validate your load balancing’s working correctly? Not really.
Complex logic: When you need sophisticated decision-making based on network state, Ansible playbooks become unwieldy fast.
Network understanding: Ansible doesn’t understand network protocols. It sees CLI output as text, not as routing tables or interface states.
I spent three days once trying to get Ansible to properly validate a multi-area OSPF deployment. The playbook was 200 lines of templates and regex patterns, and it still missed edge cases. Absolute pain.
When to Use Ansible
Use Ansible when you need to:
- Apply consistent configurations across many devices
- Manage configuration compliance and drift
- Integrate with existing IT automation (since everyone knows Ansible)
- Push emergency config changes quickly
- Replace repetitive manual configuration tasks
Don’t use Ansible for complex testing, validation, or anything requiring deep network protocol understanding.
NAPALM: The Multi-Vendor Abstraction Layer

NAPALM (Network Automation and Programmability Abstraction Layer with Multivendor support) takes a different approach. It’s all about vendor abstraction and basic network operations.
What NAPALM Does Well
Vendor neutrality: Same code works across Cisco, Juniper, Arista, others. Write once, run everywhere.
Operational focus: Built for network operations – getting device facts, configuration management, basic validation.
Python integration: Easy to integrate into larger Python applications. Loads of network engineers already know some Python.
Configuration sessions: Proper transaction support with rollback capabilities. Much safer than raw CLI commands.
# This is typical NAPALM - clean and vendor-agnostic
from napalm import get_network_driver
driver = get_network_driver('iosxr')
device = driver('172.16.1.10', 'dickie1', 'password123')
device.open()
facts = device.get_facts()
interfaces = device.get_interfaces()
device.close()
# Same code works on Juniper, just change the driver
I’ve used NAPALM loads for basic automation tasks. Really nice when you’ve got a mixed vendor environment and need consistent interfaces.
Where NAPALM Falls Short
Limited testing capabilities: NAPALM can get basic facts and configs, but complex network testing? Not its strong suit.
Parsing limitations: Limited parsers compared to what you get with pyATS. Often you’re still dealing with raw CLI output.
No test framework: NAPALM’s a library, not a testing framework. You’ll need to build your own test structure around it.
Protocol validation: Can’t do sophisticated protocol testing or validation. It’s really just a glorified CLI abstraction layer.
When to Use NAPALM
Use NAPALM when you:
- Need simple multi-vendor automation
- Want to integrate network operations into Python applications
- Need basic configuration and fact gathering
- Want safer configuration changes with rollback support
- Don’t need complex testing or validation
Nornir: The Python-Native Framework

Nornir’s the new kid on the block, designed specifically for network automation using Python. It’s what you get when Python developers build a network automation framework from scratch.
What Nornir Does Well
Pure Python: No YAML, no domain-specific languages. Just Python code, which means proper debugging, testing, error handling.
Parallel execution: Built for speed. Can run tasks across hundreds of devices simultaneously.
Flexible inventory: Your device inventory can come from anywhere – files, databases, APIs, whatever.
Plugin architecture: Easy to extend with custom plugins. Much more flexible than rigid playbook structures.
# Nornir's approach - pure Python
from nornir import InitNornir
from nornir.plugins.tasks.networking import netmiko_send_command
nr = InitNornir(config_file="config.yaml")
def check_bgp_status(task):
result = task.run(task=netmiko_send_command,
command_string="show bgp summary")
# Now you can do proper Python logic on the results
if "Established" in result.result:
print(f"{task.host}: BGP is up")
else:
print(f"{task.host}: BGP issues detected")
nr.run(task=check_bgp_status)
Where Nornir Struggles
Steep learning curve: If you don’t know Python well, Nornir’s going to be tough. No simple YAML templates to copy.
Limited network understanding: Like NAPALM, it doesn’t really understand network protocols. You’re still parsing CLI output manually.
No test framework: It’s an automation framework, not a testing framework. You’ll need to build testing concepts yourself.
Smaller community: Fewer examples and plugins compared to Ansible or pyATS.
When to Use Nornir
Use Nornir when you:
- Are comfortable with Python development
- Need maximum flexibility and control
- Want to integrate deeply with existing Python applications
- Need high-performance parallel execution
- Don’t want to be constrained by YAML or playbook structures
pyATS: The Network Testing Specialist

Now we get to pyATS, and this is where things get interesting. pyATS wasn’t adapted from server automation – it was built specifically for network testing and validation.
What Makes pyATS Different
Network-first design: Built by network engineers for network engineers. Understands protocols, device states, network relationships.
Proper testing framework: Not just automation – actual test-driven development for networks. Write tests first, then validate your network meets them.
Massive parsing library: Thousands of parsers for network commands across multiple vendors. Structured data, not regex hell.
Production-ready: Cisco uses this internally. It’s not a lab toy – it handles real networks with thousands of devices.
State comparison: Can capture network state, make changes, then validate what actually changed. Brilliant for change management.
# This is what proper network testing looks like
from pyats import aetest
from pyats.topology import loader
class TestBGPNeighbors(aetest.Testcase):
@aetest.test
def test_bgp_established(self, testbed):
for device in testbed:
bgp_summary = device.parse('show bgp summary')
for neighbor in bgp_summary['bgp_id']['vrf']['default']['neighbor']:
state = bgp_summary['bgp_id']['vrf']['default']['neighbor'][neighbor]['session_state']
assert state == 'Established', f"BGP neighbor {neighbor} not established"
Where pyATS Excels
Complex validation: Can test network behaviour, not just configuration. Does failover work? Are convergence times acceptable? How’s traffic flowing?
Before and after testing: Capture state before changes, make changes, verify what actually changed. Brilliant for maintenance windows.
Multi-vendor support: Works across vendors with the same test code. No more writing separate scripts for each platform.
Enterprise scale: Handles large networks with sophisticated reporting and test orchestration.
I once used pyATS to validate a data centre migration. We captured the entire network state before moving workloads, then validated that connectivity, performance, and redundancy all worked exactly the same afterwards. Caught three issues that would’ve caused outages.
Where pyATS Has Limitations
Learning curve: It’s a proper testing framework. Takes time to learn the concepts and structure.
Overkill for simple tasks: If you just need to push the same config to 10 switches, pyATS is probably overkill.
Testing focus: It’s designed for testing and validation. If you just need configuration management, other tools might be simpler.
When to Use pyATS
Use pyATS when you:
- Need proper network testing and validation
- Want to implement test-driven network development
- Need to validate complex network behaviors
- Are managing enterprise-scale networks
- Want to catch issues before they impact users
- Need detailed change validation and reporting
The pyATS vs Ansible Decision Tree
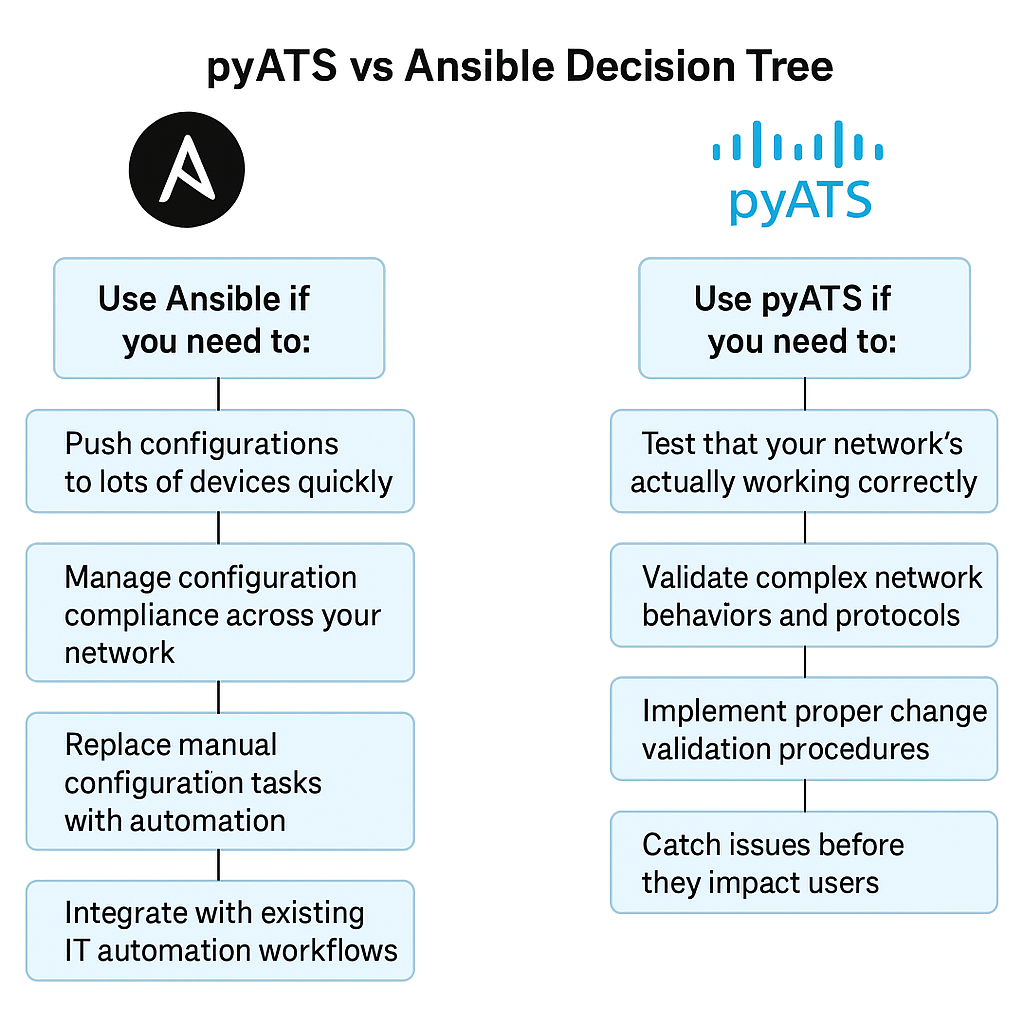
Since this is the comparison I get asked about most, let me break it down simply:
Use Ansible if you need to:
- Push configurations to lots of devices quickly
- Manage configuration compliance across your network
- Replace manual configuration tasks with automation
- Integrate with existing IT automation workflows
Use pyATS if you need to:
- Test that your network’s actually working correctly
- Validate complex network behaviors and protocols
- Implement proper change validation procedures
- Catch issues before they impact users
Why not both? Actually, loads of organizations use both. Ansible for configuration management, pyATS for testing and validation. They solve different problems.
Real-World Examples from My Experience
Let me share some actual scenarios where I’ve seen these tools used successfully (and some disasters where the wrong tool was chosen).
Scenario 1: Data Centre Network Refresh
Challenge: Replace 50 old switches with new ones, ensuring identical functionality.
Wrong approach: Customer initially tried using Ansible to validate everything was working. Spent weeks writing complex playbooks to parse CLI output and validate protocols. Half the tests were unreliable and this was a great example of pyATS vs Ansible, using the right tool for the right job.
Right approach: Used Ansible to push baseline configs to new switches. Used pyATS to capture state from old switches, then validate new switches had identical protocol states, routing tables, and connectivity. Worked brilliantly.
Scenario 2: Security Compliance Automation
Challenge: Ensure 200 branch routers all comply with security baseline.
Right tool: Ansible was perfect here. Created playbooks to check and remediate configuration drift. Simple, effective, exactly what Ansible’s designed for.
Scenario 3: Service Provider BGP Testing
Challenge: Validate BGP behavior across multiple vendors after policy changes.
Wrong approach: Tried using NAPALM to gather BGP information and validate manually. Spent ages parsing different output formats from different vendors.
Right approach: pyATS tests that worked identically across Cisco, Juniper, and Arista. Same test code, different devices, consistent validation.
Scenario 4: Branch Office Automation
Challenge: Deploy new branch offices with standardized configurations.
Right combination: Nornir for the deployment orchestration (needed complex logic based on site requirements), NAPALM for vendor-neutral device interaction, pyATS for final validation that everything worked correctly.
Common Mistakes I See
Mistake 1: Using Ansible for Everything Ansible’s popular, so people try to use it for testing and validation. You’ll end up with fragile playbooks full of regex patterns that break constantly.
Mistake 2: Jumping to pyATS Too Early pyATS is powerful, but if you’re just starting with automation, begin with simpler tools. Learn the concepts, then move to more sophisticated frameworks.
Mistake 3: Not Understanding the Problem Before choosing a tool, understand what problem you’re solving. Configuration management? Testing? Device facts gathering? Different tools for different jobs.
Mistake 4: Ignoring Integration These tools can work together. Don’t think you have to choose just one. Use the right tool for each part of your workflow.
Performance and Scale Considerations
Ansible: Good for moderate scale. Playbooks can become slow with complex logic. Not designed for high-performance parallel operations.
NAPALM: Fast for basic operations. Good performance characteristics, but limited by what it can actually do.
Nornir: Excellent performance. Built for parallel execution. Can handle large-scale operations efficiently.
pyATS: Enterprise-scale performance. Designed to handle thousands of devices with sophisticated test orchestration and reporting.
Integration and Ecosystem
Ansible: Huge ecosystem. Integrates with everything. Loads of existing playbooks and roles available.
NAPALM: Good Python ecosystem integration. Works well as part of larger Python applications.
Nornir: Pure Python, so integrates well with any Python-based tools and workflows.
pyATS: Strong integration with Cisco ecosystem. Growing integration with CI/CD tools and monitoring systems.
Learning Path Recommendations
If you’re just starting with network automation:
- Start with Ansible – Learn the basic concepts of network automation. Ansible’s got loads of examples and a gentle learning curve.
- Add NAPALM – Once you understand the basics, NAPALM teaches you about vendor abstraction and programmatic device interaction.
- Explore Nornir – If you’re comfortable with Python, Nornir shows you what’s possible with pure Python automation.
- Master pyATS – When you need proper testing and validation, pyATS is the professional-grade solution.
Don’t try to learn everything at once. Each tool teaches you different concepts and approaches.
Decision Framework: Choosing the Right Tool
While their has been a lot of talk about pyATS vs Ansible in the post, we have learned that there are use cases for other network automation tools. Ask yourself these questions:
What’s the primary goal?
- Configuration management → Ansible or Nornir
- Testing and validation → pyATS
- Basic device interaction → NAPALM
- Complex automation logic → Nornir or pyATS
What’s your team’s skill level?
- New to automation → Ansible
- Comfortable with Python → Nornir or pyATS
- Need quick wins → NAPALM for simple tasks
What’s the scale?
- Small networks → Any tool works
- Enterprise scale → pyATS or Nornir
- Need parallel execution → Nornir
What’s the environment?
- Single vendor → Any tool
- Multi-vendor → NAPALM or pyATS
- Mixed with server automation → Ansible
Advanced Use Cases and Combinations
In practice, most mature automation teams use multiple tools:
Configuration Management Pipeline:
- Ansible pushes configurations
- pyATS validates they’re working correctly
- Monitoring systems alert if tests fail
Change Management Workflow:
- pyATS captures pre-change state
- Ansible applies configuration changes
- pyATS validates post-change state
- Report shows exactly what changed
Development Workflow:
- Nornir handles complex deployment logic
- NAPALM provides vendor abstraction
- pyATS validates the deployed services work correctly
Common Integration Patterns
Ansible + pyATS: Ansible for config management, pyATS for validation. Very common pattern in enterprise environments and this does away with the pyATS vs Ansible debate when they exist in the same network.
Nornir + NAPALM: Nornir for orchestration and complex logic, NAPALM for device interaction. Good for custom automation applications.
CI/CD + pyATS: Git triggers automated tests using pyATS when configs change. Prevents bad configs from reaching production.
Troubleshooting and Debugging
Ansible: YAML debugging can be frustrating. Limited visibility into complex logic flow.
NAPALM: Good Python debugging tools. Easy to troubleshoot since it’s just Python code.
Nornir: Excellent debugging since it’s pure Python. Can use standard Python debugging tools and techniques.
pyATS: Sophisticated logging and reporting. Detailed test results make troubleshooting straightforward.
Future-Proofing Your Skills
The automation landscape’s constantly evolving. Here’s what I think about future-proofing:
Ansible will remain popular for configuration management. It’s embedded in too many organisations to disappear.
NAPALM fills a specific niche for vendor abstraction. Useful for basic automation needs.
Nornir represents the Python-native approach. As more network engineers learn Python, this’ll become more popular.
pyATS is the professional-grade testing solution. As networks become more complex, proper testing becomes essential.
My advice? Learn the concepts behind each tool, not just the syntax. The specific tools will evolve, but the underlying principles remain constant.
Wrapping Up: Choose the Right Tool for the Job
Look, there’s no single “best” automation tool. Each one solves different problems:
- Ansible for configuration management and getting started with automation
- NAPALM for vendor-neutral device operations
- Nornir for Python-based automation with maximum flexibility
- pyATS for proper network testing and validation
The pyats vs ansible debate misses the point. They’re solving different problems. Ansible pushes configs, pyATS validates they work. You probably need both.
Don’t be like me when I started – trying to use Ansible for everything because it was the only tool I knew. Took me months to realise I was using a hammer for screws.
Start with understanding what problem you’re trying to solve. Then choose the tool that’s designed for that problem. Your future self will thank you for not trying to force the wrong tool into the wrong job.
And remember – these tools can work together. Don’t think you have to choose just one. Build a toolkit that solves your actual problems, not the problems you think you should have.
Most importantly, start simple and build up complexity gradually. We have seen that the pyats vs ansible debate is not clear cut anymore, they are no longer the only two automation players people are talking about.
Network automation’s like learning to drive – you don’t start with a Formula 1 car. Master the basics with simpler tools, then move to more sophisticated ones when you actually need the extra capabilities.
Learn more about network automation tool comparisons at Network to Code

Pingback: Blog Index: Cisco pyATS Automation - RichardKilleen
Great distinction between pyATS and Ansible – I’ve definitely seen teams try to shoehorn validation tasks into Ansible when it’s clearly not designed for that. This kind of guidance really helps avoid costly missteps early in automation projects.
Pingback: Learn Python for Network Engineers: Blog 1 - RichardKilleen